Last part we have gone through the DB changes and RPD configuration for implementing data level and object level securities. Now there are some final pieces that needs to be done in order to make this implementation perfect. Let's start with object level security. We need to set them up so that different user group will only have access to their dashboards first.
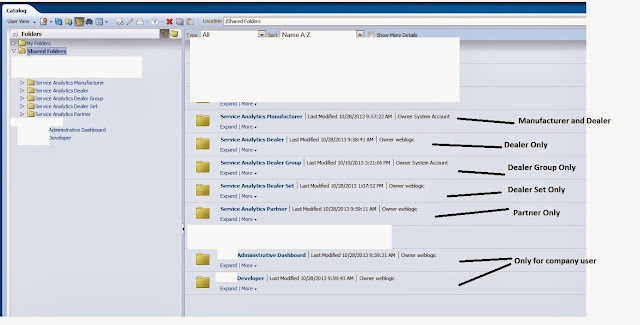
So here are the different folders that stores dashboards and reports meant for different users.
As you can see, I already know what kind of access each folder should have as shown below:
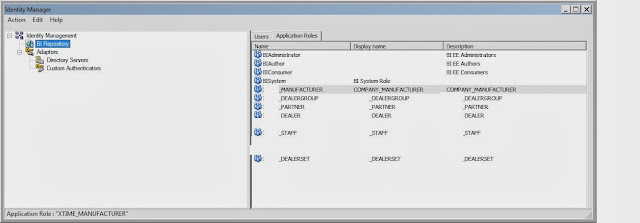
I will show you what I did for manufacturer and dealer group folders. Each will be assigned to the proper application roles with the right level of privileges:
Same idea for partner and dealer folders, which I am going to skip now. For internal user, the below is the configuration:
There are other dashboard objects that allows permission setting, this will further controls object level access based on user groups. I am going to skip all these steps now.
For testing, let's see how things are working when these different users log in:
1. Manufacturer user logs in:
Object level Security working:
Data level security working:
2. Dealer Group user logs in:
Object level security working:
Data level security working:
For data level security, this user is unrestricted, so he can see all data:
So here are the different folders that stores dashboards and reports meant for different users.
As you can see, I already know what kind of access each folder should have as shown below:
I will show you what I did for manufacturer and dealer group folders. Each will be assigned to the proper application roles with the right level of privileges:
Same idea for partner and dealer folders, which I am going to skip now. For internal user, the below is the configuration:
There are other dashboard objects that allows permission setting, this will further controls object level access based on user groups. I am going to skip all these steps now.
For testing, let's see how things are working when these different users log in:
1. Manufacturer user logs in:
Object level Security working:
Data level security working:
2. Dealer Group user logs in:
Object level security working:
Data level security working:
3. Other user groups are working the same way, I am gonna skip posting the screenshots.
Let's look at company internal user logging in:
For object level security, this user is unrestricted so all dashboards are accessible:
For data level security, this user is unrestricted, so he can see all data:
Thanks
Until next time